There are several different ways to set up risk verification in Operational Risk. The method described here may be considered best practice for verification of critical control measures.
After critical risks have been identified and assessed for an organization, a list of base controls that protect against these critical risks can be identified for verification. The purpose of verification is to ensure that the base controls are fit for purpose, and that they are maintained and managed so that they will work as expected.
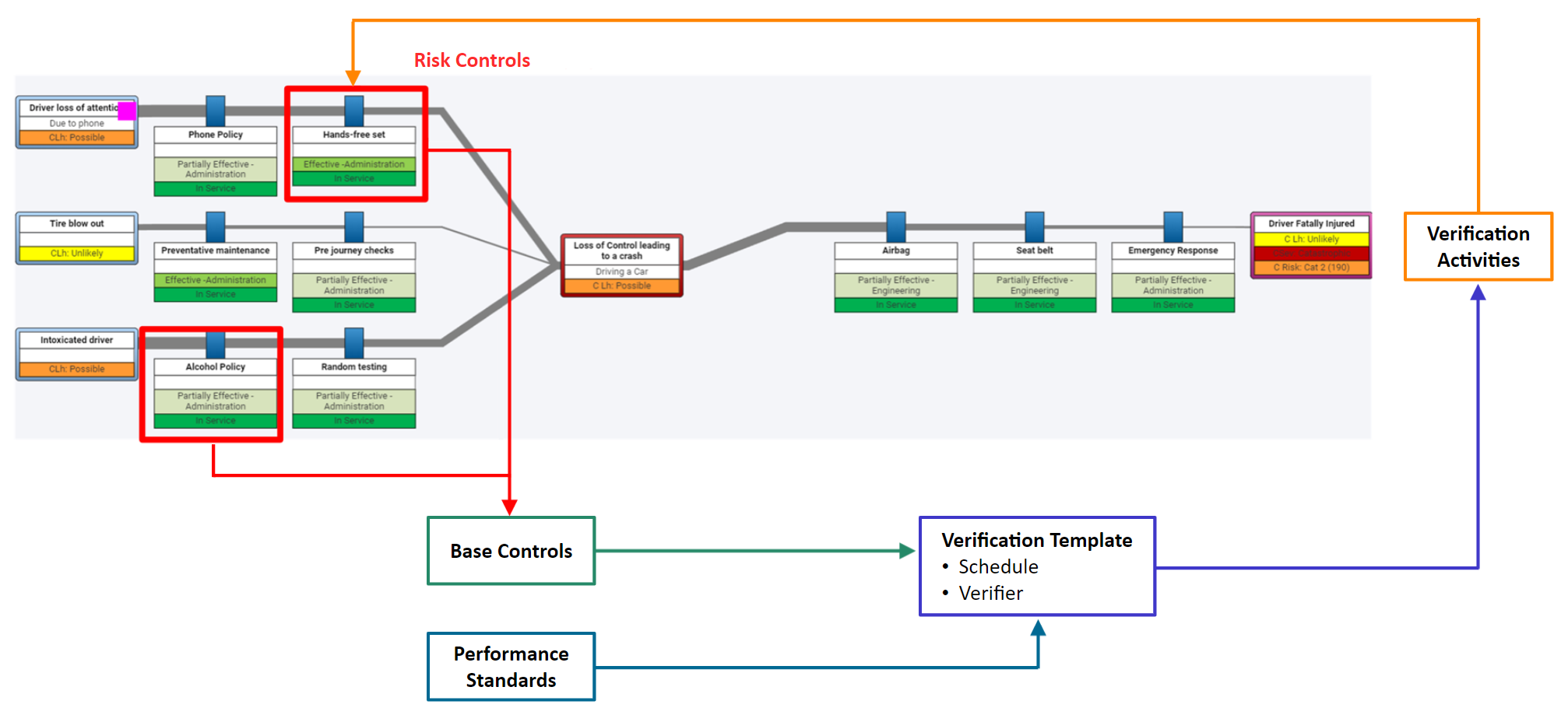
The image below shows how critical controls can be verified in Operational Risk.
This example has the following components:
- Risk controls are visible in the bowtie. Each is a unique item in the system, with its own context and effectiveness. There are often multiple risk controls across different bowties, or within the same bowtie, that refer to the same unique control at a site/business. The effectiveness of that control measure is dependent on the risk scenario, so it may have different context, independence, and effectiveness for different causes, consequences, and bowties with Operational Risk.
- Base controls link to individual controls. There should be only one base control per actual control in the bowtie.
- Performance standards prompt a person who is responsible for verifying a base control to answer a series of questions to complete the verification activity.
- Verification templates link a base control with a performance standard, as well as a schedule for generating verification activities and an individual user in the system who is assigned to complete those activities. A single base control may be linked with multiple verification templates to allow for different verification scenarios.
- Verification activities are generated from verification templates. When verification activities are complete, the results link back to the individual risk controls associated with the base control that has been verified. This way, the verification results are visible in the bowtie risk assessments themselves, making them “live” documents that are useful for reporting on and managing risks.
Was this helpful?
Yes
No
Thanks for your feedback!