Role Management in Accelerate
Roles are a collection of polices; a role can have one or many policies. Roles are assigned to a user at a location, and users can be assigned multiple roles.
Policies are a collection of permissions that can be added to a role; a policy can have one or many permissions. Policies cannot be edited.
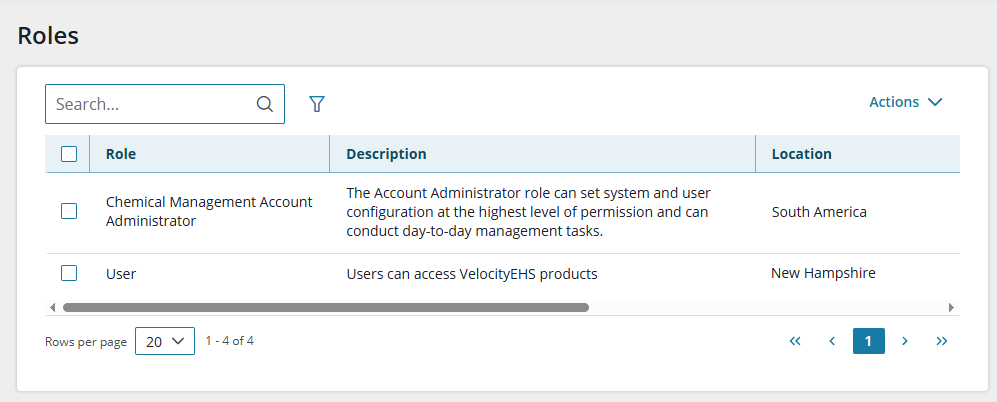
Chemical Management has four system roles, which can not be edited:
| Role | Description |
| Chemical Management Account Administrator | The Account Administrator role can set system and user configuration at the highest level of permission and can conduct day-to-day management tasks. |
| Chemical Management Administrator | The Administrator role can set system configuration and can conduct day-to-day management tasks. |
| Chemical Management Manager | The Manager types may have location-specific rights and can conduct day-to-day management tasks. |
| Chemical Management General User | The General User role can have location-specific rights and read-only access to SDSs. |
Users can add new roles, and can clone System Roles to create custom roles that meet the their needs. Adding a role creates a new role with no policies assigned, and cloning (copying) a role creates a new role with policies already assigned. Policies can be assigned to or unassigned from these roles.
See Accelerate Roles and Permissions for more information.
Locations and Roles
Chemical Management will only display locations in the location hierarchies to which a user’s role is assigned in Accelerate. For example, this user is assigned roles only at the South America and New Hampshire locations:
Location-Specific Policies
Some policies are exercised only at locations to which the role is assigned. For example, if your role is assigned only at the Boston location and you are trying to “ban chemicals” for New York, you will not be able to do so.
For policies that are not location-specific, Chemical Management users have the maximum permissions assigned. For example, to change the product name on SDS document, a user need only be assigned that policy at one of their assigned locations to be able to change the product name at all of their assigned locations.
The following policies are assigned to the Chemical Management Account Administrator, Administrator, and Manager roles:
- View approval records in the Inventory Module
- Manage Containers
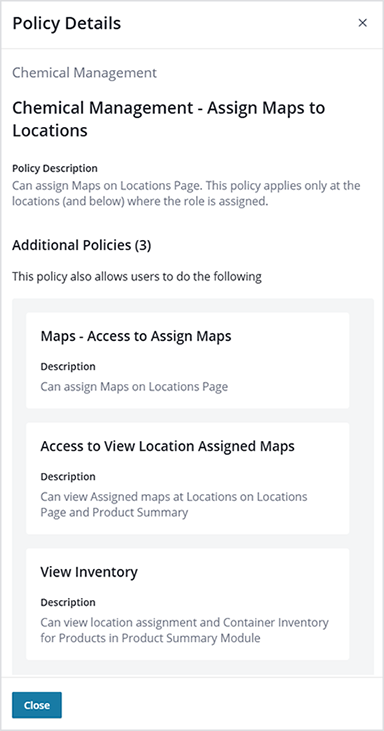
- Assign Maps to Locations
- Edit Maps
- SDS Document Request Email Eligibility
- Workflow Approver
The “Can mark an Inactive Container as Active” policy is assigned to all four system roles.
Product Specific Features
All available policies can be assigned to roles. However, some policies are made just for Chemical Management (HQregxr) customers.
If you assign these Chemical Management policies to a user who only has an SDS account, they won’t have permission to use them.
The following policies do not apply to SDS-only customers:
Chemical Risk Assessment
- Create, review, and delete COSHH risk assessments
- Print COSHH risk assessments
- View COSHH risk assessments
Ingredient Level of Concern
- View ingredient level of concern details
PFAS Indicator
- Manage PFAS
- View PFAS
These limitations are explained in the policy descriptions.
Additional Policies
Policies can have Additional Policies, policies that are also provided within a Policy. For example, if you assign the “Can Ban Chemical” Policy to a role, with that policy you are also providing the role the eBinder Access Policy, SDS Search Access Policy and View Ingredients and Ability to index-ingredient Policies.
Additional policies are added to the main policy so that a user can complete all the necessary functions of banning chemicals. In this example, the “Assign Maps to Locations” policy has three additional policies:
Best Practices for Role Assignments for Users
To make it easier to update roles for your users, we recommend this process:
- Clone the Chemical Management System Role.
- Rename the cloned role.
- Assign the cloned role to your users.
When you want to make a change to the policies in a role, just update the cloned role. All users with that role will automatically get the policy change.